HackTheBox | MoneyFlowz
Challenge Description:
Frank Vitalik is a hustler, can you figure out where the money flows?
Initial Recon
All HTB gave us is a name, so I can’t think of anything better than to just put that name into google. The very first result looks promising. We have a reddit post by /u/frankvitalik talking about a crypto scam, and the challenge is called “MoneyFlowz.”
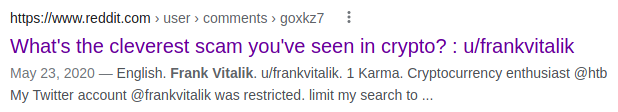
Here’s the actual reddit post:
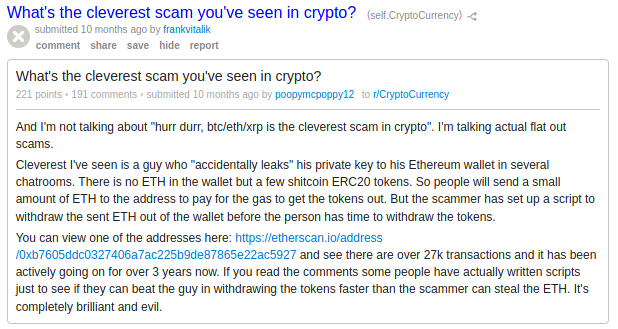
The post doesn’t really have anything of value, the link leads to a list of transactions but I couldn’t find anything really useful there. I decided to check his reddit post history to see if he had any other posts and sure enough:
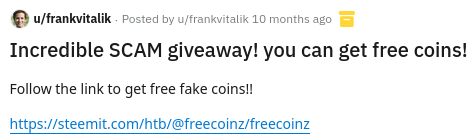
Investigating the Scam link
Following that link, we’re taken to a page that has an etherium wallet address (0x1b3247Cd0A59ac8B37A922804D150556dB837699) and outlines what is essentially the classic RuneScape gold doubling scam: send me some money and I’ll get you twice as much back. There’s nothing else of value on the page, but the poster did take the effort to leave a comment on his own post.
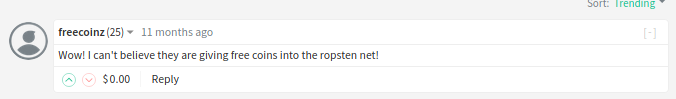
Looks like back to google we go because I have no idea what ropsten net is. But context tells me it has to do with eth.
Following the Money
Going to that site looks like we can input a wallet address and see all the transactions involving that wallet, so I’ll just input the wallet link from the initial scam page and see what we get.
We get back every transaction involving that wallet, 97 in total as of the writing of this post. Every transaction looks the same, IN to the wallet address we found in the Scam post:
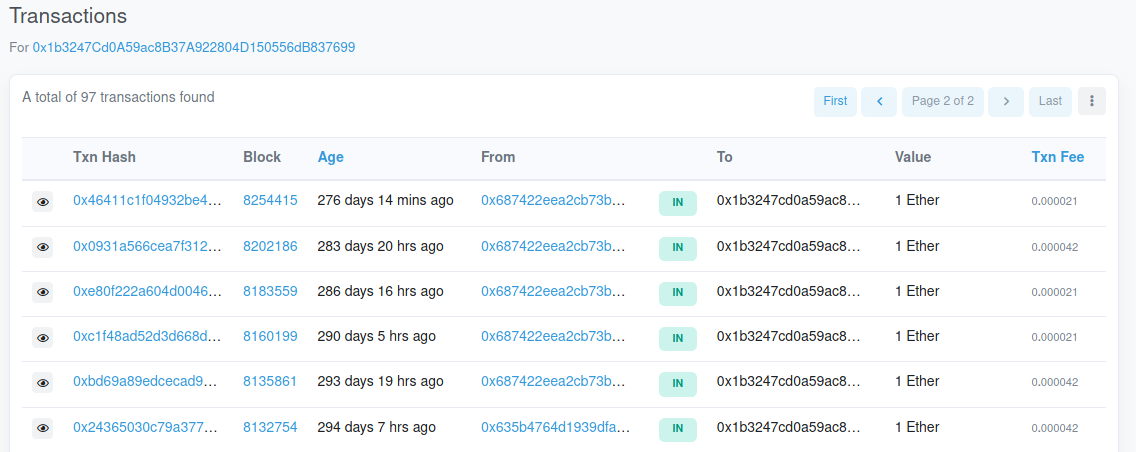
…but all the way at the bottom there are some interesting transactions that don’t fit in. This one has an OUT to a different wallet from the one originally listed in the scam.
![]()
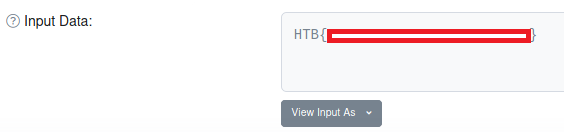
If we drill-down into this transaction, we see a hex value in the Input Data field, and the site allows us to change the input encoding directly… how convenient.
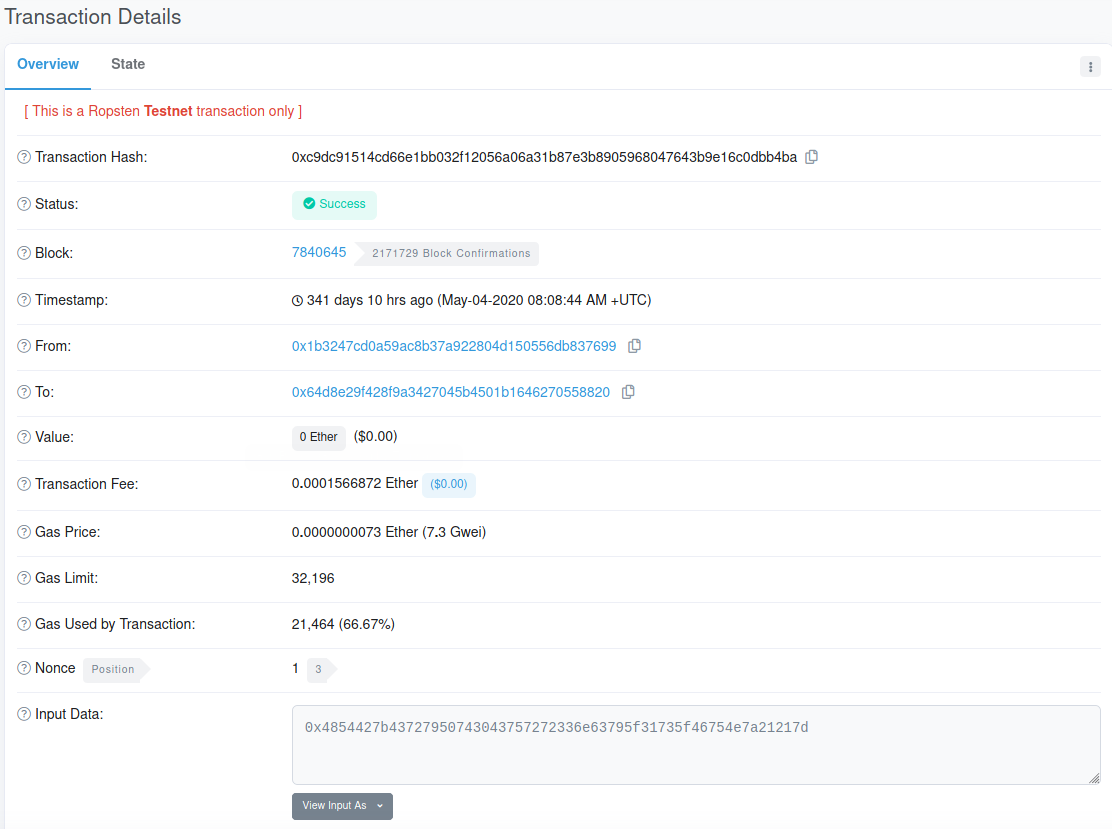
Finally, we reach our flag.
What can we learn from this?
OSINT is a very effective method of performing passive reconnaissance, without taking up too much time or effort. We don’t need any special tools to do this, we just need to be methodical in our approach. Solving a problem becomes significantly easier when you know what questions to ask.