TryHackMe | Corridor

Challenge Description:
You have found yourself in a strange corridor. Can you find your way back to where you came?
In this challenge, you will explore potential IDOR vulnerabilities. Examine the URL endpoints you access as you navigate the website and note the hexadecimal values you find (they look an awful lot like a hash, don’t they?). This could help you uncover website locations you were not expected to access.
Initial Recon
We’ll start by doing basic web application reconnaissance (a long way of saying “let’s look at the source”). Immediately, we can see some very interesting values, which were hinted to us in the challenge description.
Data of Interest
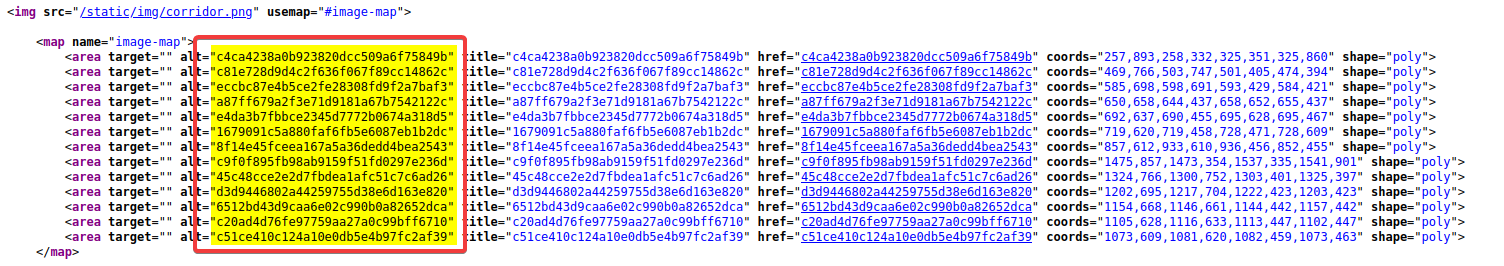
Now, copy pasting these one at a time is going to be a huge pain - so let’s use something like CyberChef to carve these values out. To do that you can use the following formula:

Finding a Pattern
From here, we can leverage something like CrackStation to see if any of these have known values:
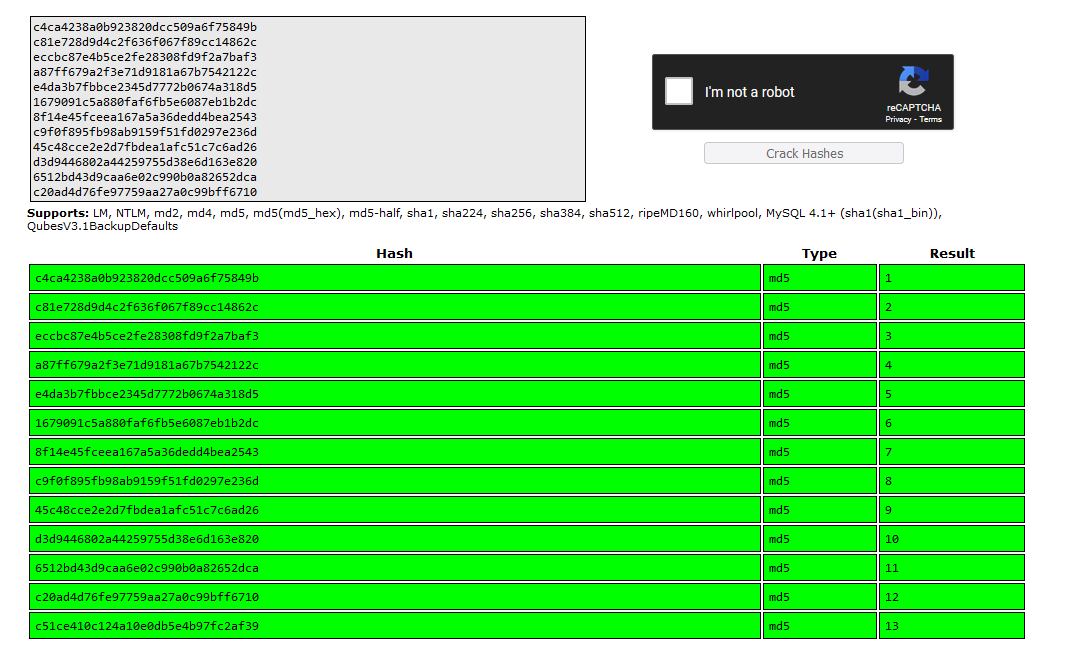
So we can see an easily recognizable pattern in these hashes, and so I thought “well the flag is obviously just the next number!”. Well, it wasn’t. Trying the next number in the pattern just takes you to an “empty room”.
There has to be a better way
I tried the next one, and the next one, and the next one, and still wasn’t getting anywhere. So… I decided that the number must be an insane value, and I’d probably need to script it… so I did. I wrote a simply python script that would iterate every integer, generate an md5 hash, and then send a crafted HTTP request to the site to try and get the flag this way. I let this script run for a few minutes and still nothing.
Finally, I decided that it might actually be in the opposite direction. And uh… yeah, let’s just say I regret not falling back to my computer science days in terms of what index arrays start at (for most languages).
I decided to let the script run in reverse:
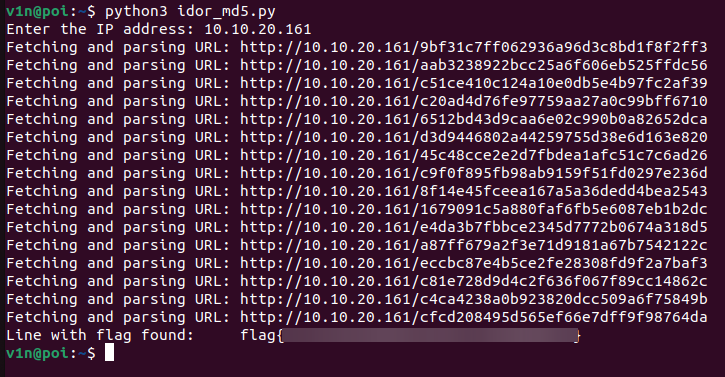
Example Script
I still think that the process of scripting this out was a valuable lesson, because it could very well have been an insanely large number, and the idea of manually trying every integer’s md5 was NOT appealing.
Here is an example of how this type of attack could be scripted out: